See our Intelligence in Action
Main Pages
Services
Design by Ariel for BYQ Studio

Stop adding more data.
Start deciding.
Three layers of orbital intelligence that don't just tell you what's happening, they tell you exactly what to do about it.

Stop adding more data.
Start deciding.
Three layers of orbital intelligence that don't just tell you what's happening, they tell you exactly what to do about it.

The Problem
The Problem
The Problem
Supply chains operate on trust because verifying physical reality has been too
Supply chains operate on trust because verifying physical reality has been too
Supply chains operate on trust because verifying physical reality has been too
Product pillars
Product pillars
Product pillars
An integrated suite to ensure you: verify, predict, and inform.
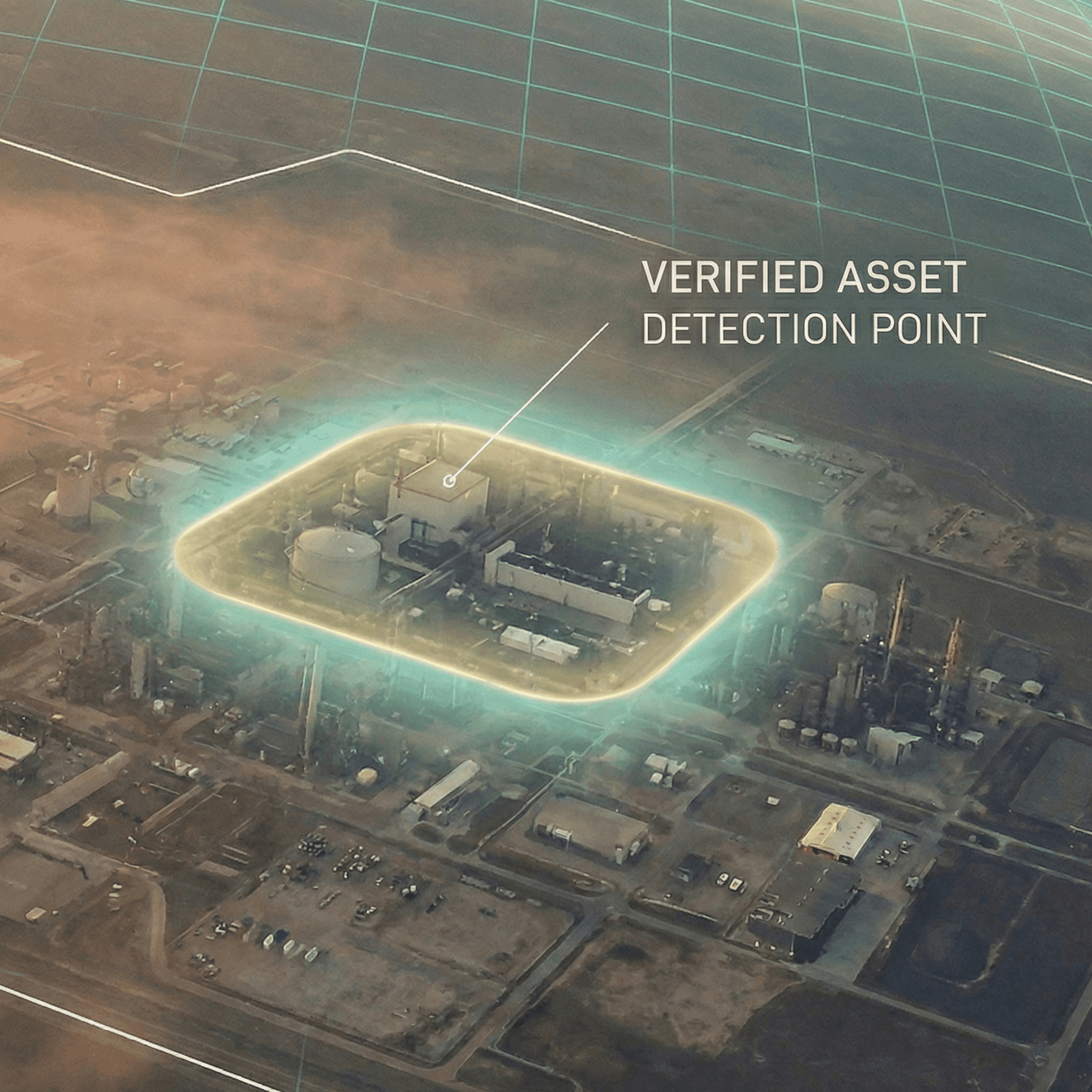
TERRAIN
Before you can trust a supplier, you need to know they physically exist. Verify every facility through orbital imagery; no more self-reported data, no more trust assumptions.
Result: 40% of new supplier applicants fail physical verification.
Pillar 01
The Filter

TERRAIN
Before you can trust a supplier, you need to know they physically exist. Verify every facility through orbital imagery; no more self-reported data, no more trust assumptions.
Result: 40% of new supplier applicants fail physical verification.
Pillar 01
The Filter

TERRAIN
Before you can trust a supplier, you need to know they physically exist. Verify every facility through orbital imagery; no more self-reported data, no more trust assumptions.
Result: 40% of new supplier applicants fail physical verification.
Pillar 01
The Filter
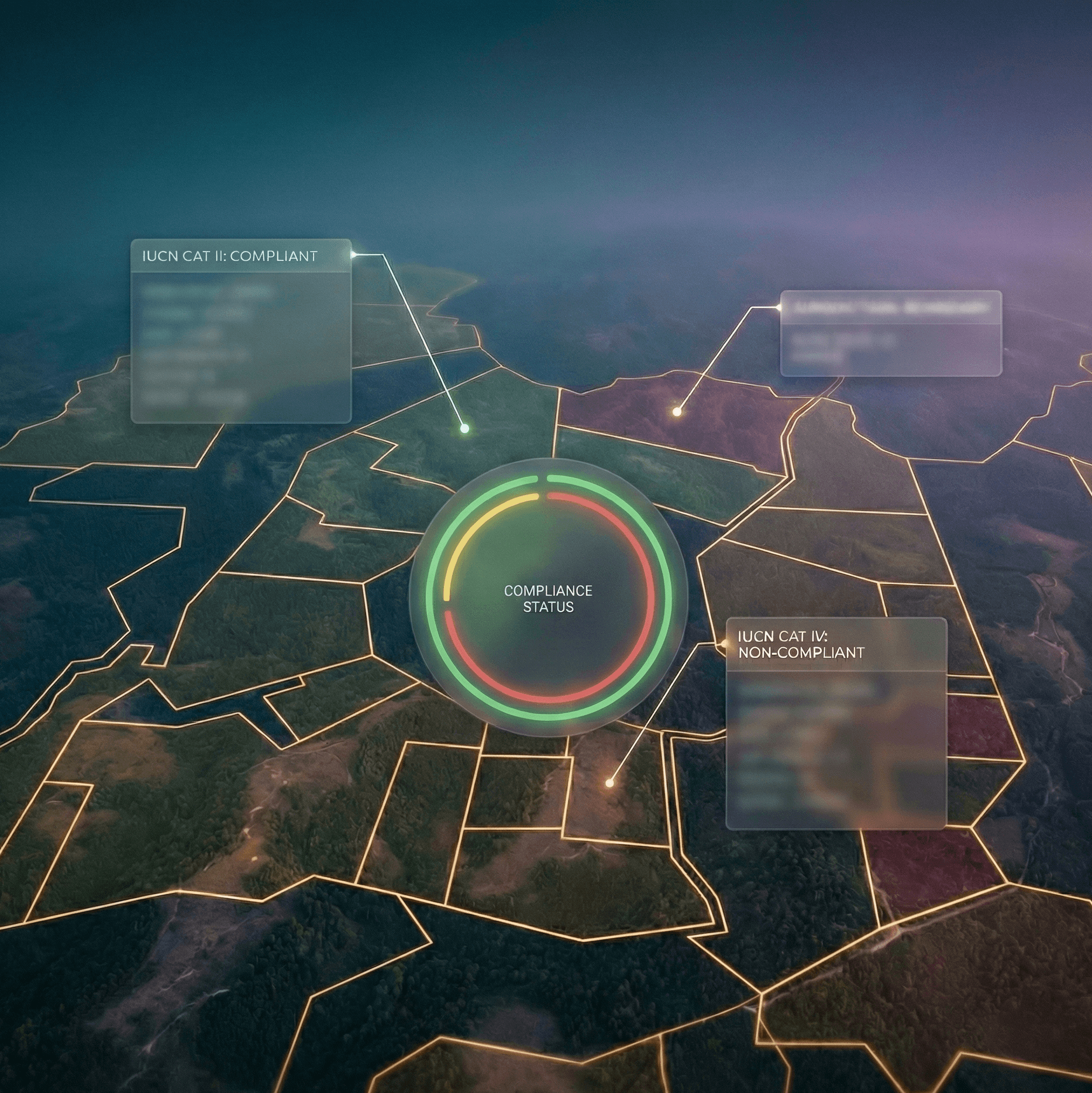
RANGER
Every verified asset is automatically mapped against +190 global regulatory frameworks. Generate audit-ready citations with article numbers.
Result: Compliance documentation generated in seconds, not weeks.
Pillar 02
The Legal Layer

RANGER
Every verified asset is automatically mapped against +190 global regulatory frameworks. Generate audit-ready citations with article numbers.
Result: Compliance documentation generated in seconds, not weeks.
Pillar 02
The Legal Layer

RANGER
Every verified asset is automatically mapped against +190 global regulatory frameworks. Generate audit-ready citations with article numbers.
Result: Compliance documentation generated in seconds, not weeks.
Pillar 02
The Legal Layer
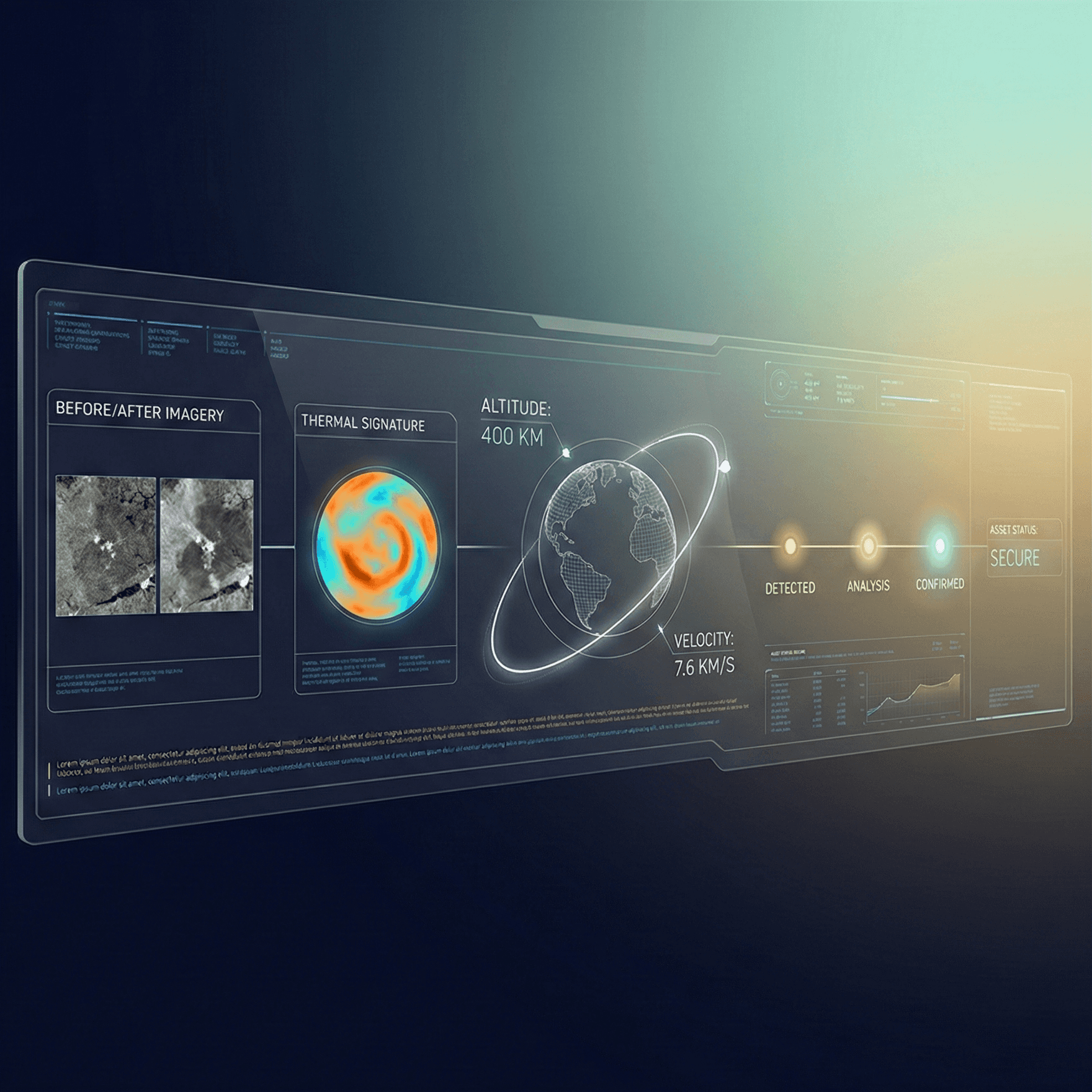
RECON
Continuous satellite monitoring detects operational changes before they become supply chain disruptions. See 8 weeks into the future with predictive intelligence.
Result: Average 8-week lead time on disruption events.
Pillar 03
The Insight

RECON
Continuous satellite monitoring detects operational changes before they become supply chain disruptions. See 8 weeks into the future with predictive intelligence.
Result: Average 8-week lead time on disruption events.
Pillar 03
The Insight

RECON
Continuous satellite monitoring detects operational changes before they become supply chain disruptions. See 8 weeks into the future with predictive intelligence.
Result: Average 8-week lead time on disruption events.
Pillar 03
The Insight

The Problem
Supply chains operate on trust because verifying physical reality has been too
Product pillars
An integrated suite to ensure you: verify, predict, and inform.

TERRAIN
Before you can trust a supplier, you need to know they physically exist. Verify every facility through orbital imagery; no more self-reported data, no more trust assumptions.
Result: 40% of new supplier applicants fail physical verification.
Pillar 01
The Filter

RANGER
Every verified asset is automatically mapped against +190 global regulatory frameworks. Generate audit-ready citations with article numbers.
Result: Compliance documentation generated in seconds, not weeks.
Pillar 02
The Legal Layer

RECON
Continuous satellite monitoring detects operational changes before they become supply chain disruptions. See 8 weeks into the future with predictive intelligence.
Result: Average 8-week lead time on disruption events.
Pillar 03
The Insight
Capabilities
Capabilities
Capabilities
Capabilities
What you can do with OpenAtlas
What you can do with OpenAtlas
ID Ghost Suppliers
Protect your business from fraud by flagging suppliers with no verified physical presence before engaging with them.
ID Ghost Suppliers
Protect your business from fraud by flagging suppliers with no verified physical presence before engaging with them.
At-Risk Supply Lines
Prevent supply chain disruptions with advance warnings that give you time to secure critical alternative suppliers.
At-Risk Supply Lines
Prevent supply chain disruptions with advance warnings that give you time to secure critical alternative suppliers.
Financial Impact
Quantify supply chain risks in clear dollar amounts to prioritize action, secure budget approval, and protect your bottom line.
Financial Impact
Quantify supply chain risks in clear dollar amounts to prioritize action, secure budget approval, and protect your bottom line.
Regulatory Violations
Stay compliant and avoid costly penalties with legal citations mapped to your assets across 190+ regulatory frameworks.
Regulatory Violations
Stay compliant and avoid costly penalties with legal citations mapped to your assets across 190+ regulatory frameworks.
Risk Exposure
Make confident sourcing decisions with comprehensive risk scores that combine identity, legal, and operational signals.
Risk Exposure
Make confident sourcing decisions with comprehensive risk scores that combine identity, legal, and operational signals.
Compliance Reporting
Pass audits with confidence using one-click packages complete with satellite evidence, legal documentation, and full decision trails.
Compliance Reporting
Pass audits with confidence using one-click packages complete with satellite evidence, legal documentation, and full decision trails.
ID Ghost Suppliers
Protect your business from fraud by flagging suppliers with no verified physical presence before engaging with them.
Regulatory Violations
Stay compliant and avoid costly penalties with legal citations mapped to your assets across 190+ regulatory frameworks.
At-Risk Supply Lines
Prevent supply chain disruptions with advance warnings that give you time to secure critical alternative suppliers.
Risk Exposure
Make confident sourcing decisions with comprehensive risk scores that combine identity, legal, and operational signals.
Financial Impact
Quantify supply chain risks in clear dollar amounts to prioritize action, secure budget approval, and protect your bottom line.
Compliance Reporting
Pass audits with confidence using one-click packages complete with satellite evidence, legal documentation, and full decision trails.
ID Ghost Suppliers
Protect your business from fraud by flagging suppliers with no verified physical presence before engaging with them.
Regulatory Violations
Stay compliant and avoid costly penalties with legal citations mapped to your assets across 190+ regulatory frameworks.
At-Risk Supply Lines
Prevent supply chain disruptions with advance warnings that give you time to secure critical alternative suppliers.
Risk Exposure
Make confident sourcing decisions with comprehensive risk scores that combine identity, legal, and operational signals.
Financial Impact
Quantify supply chain risks in clear dollar amounts to prioritize action, secure budget approval, and protect your bottom line.
Compliance Reporting
Pass audits with confidence using one-click packages complete with satellite evidence, legal documentation, and full decision trails.
“We are building extraordinary AI systems, then asking them to operate blind to physical reality. The constraint on autonomous decision-making is not intelligence. It is verification.”
Harry Marshall
CEO & Founder

